The Secret History of Minnesota Part 1: Engineering Research Associates
Steve Blank
DECEMBER 11, 2023
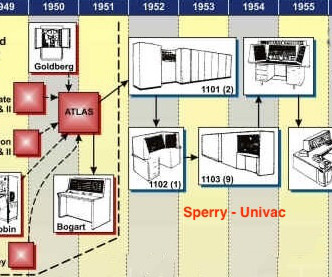
The two groups would merge in 1949 as the Armed Forces Security Agency and then become the National Security Agency (NSA) in 1952. Norris became the VP of Engineering, Engstrom the VP of Research, and Meader VP of Manufacturing. What Did ERA Build For the National Security Agency (NSA)?







Let's personalize your content